Cisco Zero Trust - The 3 W’s in Zero Trust Security
Picture this scenario: you are a security guard at an office building. Today you are looking after a restricted area. A person you’ve never seen before walks straight past you into one of the rooms. Would you stop them or would you just assume they are allowed to be there?
In a physical world, trust is most commonly based on who you are, not where you are. A savvy security guard would ask you for your ID before allowing you in. Virtually, though, the situation is different: being in the right place is often enough. If you are inside of a company’s network perimeter, it is often assumed you have the right to be there. You gain access to the same data and tools that any other trusted user would. It’s clear that such an approach is no longer enough.
Zero trust security comes in as an alternative model, more in line with the current threat landscape. It is based on the principle of “always check, never trust“, originally introduced by Forrester. It takes into account 3 main factors:
- Workforce: Employees are at risk of identity theft, which is one of the most widespread types of fraud today.
- Workload: New vulnerabilities in applications and their improper management open highways for cybercriminals.
- Workplace: With more and more connected devices, the workspace has extended far beyond the four walls of you company building.
Moving from a perimeter model to Zero Trust means assessing, adapting and implementing new security policies that address threats in a constantly changing environment. In this trust-centric approach access is granted to users and devices, not a network.
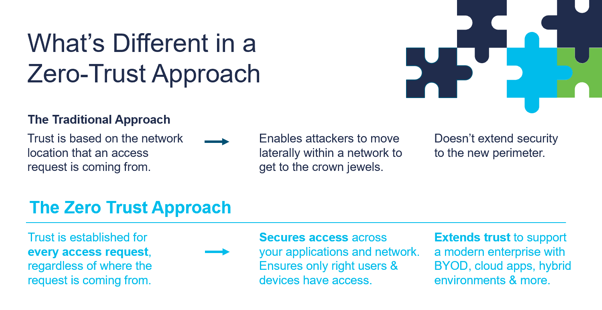
This means that policies now need to be calculated based on a vast number of data sources. All network activities must be continuously taken into account. Any indications of compromise or changes in the behaviour of apps, users and devices must be examined, validated and receive immediate responses.
How to apply a Zero Trust model
Cisco’s practical approach to Zero Trust includes six important steps.
- Establish levels of trust for users and user devices (identity verification with multi-factor authentication and device status, which must be compliant and properly updated)
- Establish levels of reliability for IoT and/or workloads (profile and baseline)
- Establish SD perimeters to control access to the application (authorised access)
- Establish SD perimeters to control access to the network (segmentation and micro-segmentation)
- Automate the adaptive policy using normalisation (network, data centre and cloud)
- Automate the adaptive policy using the response to threats (adapt the level of trust)
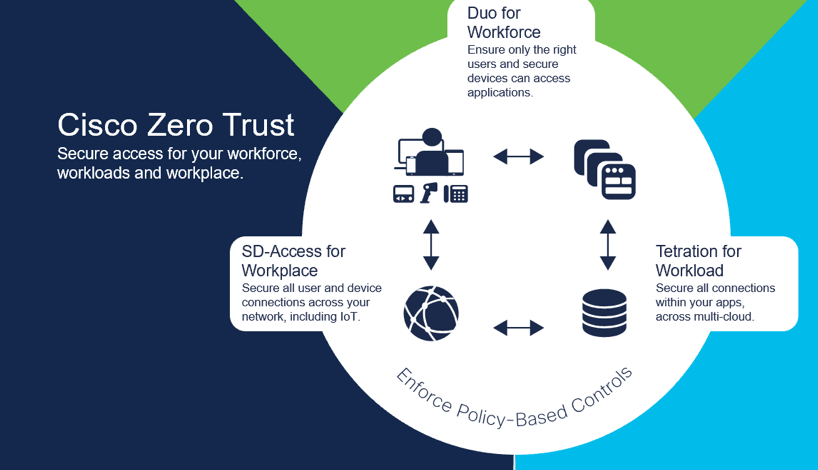
Zero Trust Security involves people, processes and technology in its adoption. It can provide a roadmap for a truly efficient and automated security infrastructure.
Contact us to discuss the right Cisco solution to suit your scaling business.